Protecting HSU’s information in the digital age is a complex challenge that includes regular monitoring of on-campus computers and educating users. It’s a system that often includes battling well-financed, sophisticated international criminals.
“There’s a community of thieves out there working together,” Callahan said. “You’ve got well-funded, international organizations, including some state-funded agencies, putting time and money into producing attacks. As long as there’s money at stake, it will be valuable for people to come up with new ways to steal information.”
Up-front education is one key to preventing problems, and at HSU and other California State University campuses, that learning comes in the form of online training. All employees are required to complete a web-based course that provides information on securing information resources.
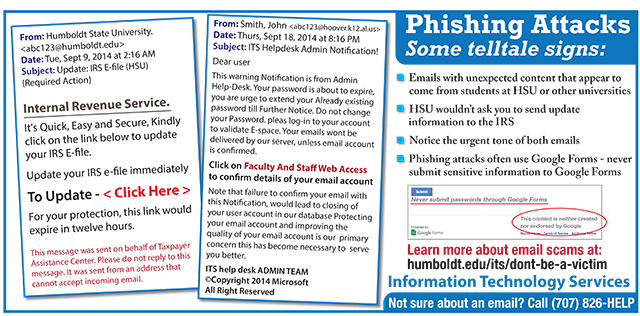
According to Callahan, the most common attack is the phishing scheme, a type of spam. Using a thinly-disguised email message, scammers hope to to mine information from users and access their account credentials. Once in, the attackers dig for social security numbers and other sensitive data before using the account to pursue other potential victims.
“There are two rounds,” Callahan said. “First, they’re trying to get your username and password. The second phase is using your account to send out a batch of emails with a fake web form that usually asks for financial information, like your bank account. And if they get access to an email account at HSU, they’ll use that to send out the phishing scheme to other universities.”
While institutions of higher education have always attracted information thieves, the availability of wireless networks opens up a more vulnerable access point. The proliferation of mobile devices and an abundance of young, technology-savvy users have made universities even more popular targets.
“We were one of the first environments where users showed up with smartphones and tablets, looking for network access,” Callahan said. “Our security engineering has had to be more varied. It’s interesting because other industries, such as healthcare and banking, are just now catching up to where we’ve been for years.”
To prevent problems, HSU’s security system uses identity protection software that constantly monitors for viruses and malware. Computer behavior patterns are also observed for warning signs of unusual activity.
Callahan and HSU Information Technology Services personnel scan for telltale signs of criminal activity, such as unusual URLs. They also rely on lists of network addresses that have been previously associated with attacks, blocking access before potential victims are infiltrated.
“We’re seeing more bursts of activity instead of the consistent attacks,” Callahan said.” It’s hard to say what it would be if we hadn’t taken the steps we have. With what we’ve been able to build, we can quickly add new address ranges as they’re identified, and new accounts as they show up. We can react within seconds before any email has been sent out.”
Those efforts have helped diminish information security risks, says Callahan, but user responsibility remains a key to protection. Messages can still get to people’s inboxes when an attack comes through using new tactics. With that in mind, HSU Information Technology Services reminds employees and students to be aware of the following tactics:
- Look for major spelling or grammatical errors in messages that pretend to be an official HSU email. This usually occurs because many of the attacks originate from countries where English is not the common language.
- Be aware of messages saying the user must act quickly to help someone in need or to claim a prize. The intent is to take advantage of human nature, Callahan says. “People want to believe what they see in front of them. That’s a difficult trait to change.”
- Don’t cooperate with callers claiming to represent a technology-related company, like Microsoft, saying they’ve detected network activity indicating your machine is infected. If you follow the instructions they provide, the scammer will install software on your computer that allows remote access to your computer.
Following that advice and being diligent helps protect both the university and its employees from information theft and more, Callahan says.
“The overall security program goal is to make HSU a less attractive place than others to attack,” Callahan said. “If we’re reacting faster and we have better educated staff, they’ll get less out of targeting us. It’s unfortunate, but it’s the old ‘I don’t have to be faster than the bear. I just need to be faster than the person next to me who is also running from the bear.’”
More information on avoiding email scams can be found on the Information Technology Services website at humboldt.edu/its/dont-be-a-victim.